- [email protected]
- Level 26, 360 Collins Street, Melbourne, VIC - 3000
Nessus Tenable Implementation
Nessus Tenable Implementation
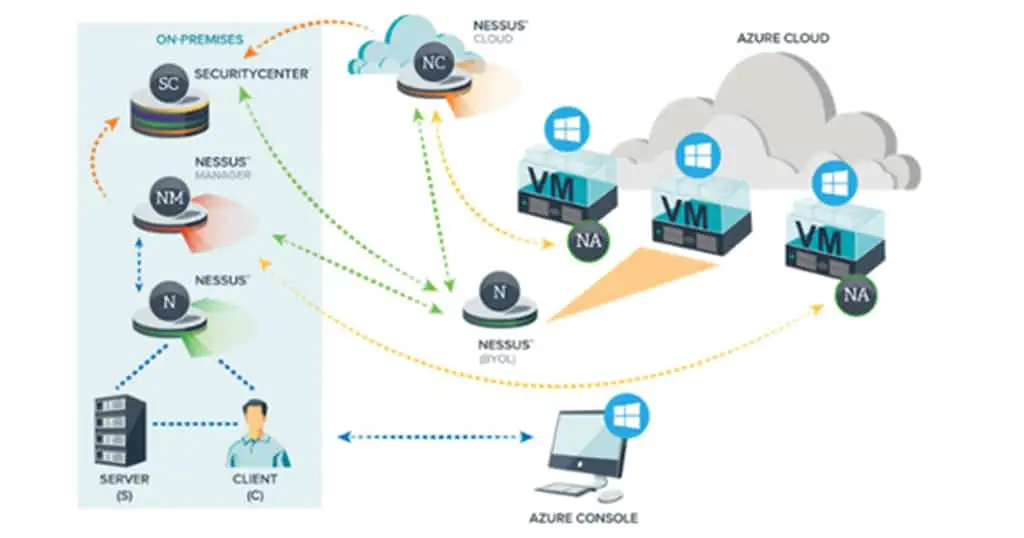
Nessus Tenable is a widely-used vulnerability assessment tool that helps organizations identify and manage security risks. Implementing Nessus effectively at Borderless CS is you can ensure a robust security posture.
By leveraging its advanced features and integrations, organizations can establish a robust defense against evolving cyber threats and following a systematic approach, organizations can strengthen their security posture, reduce risks, and maintain a resilient defense against cyber threats.

The scope of the project is:
- Assess the existing network infrastructure and prepare for Nessus implementation.
- Ensure network compatibility, firewall rules, and necessary permissions for scanning.
- Configure Nessus settings, including scan policies, authentication requirements, and target hosts.
- Integrate Nessus with existing security information and event management (SIEM) systems.
- Conduct regular vulnerability scans to identify new threats and weaknesses.
- Schedule periodic Nessus updates and patches to ensure the tool's database is current.
Nessus Tenable Implementation Disaster Recovery (DR) Service Level
| Recovery Time Objective (RTO) | Time | Comments |
|---|---|---|
| Recovery Time Objective (RTO) | 120 min | Assess the existing infrastructure and prepare the environment for Nessus implementation within 2 hours. Ensure compatibility and resource allocation. |
| Nessus Installation and Configuration | 180 min | Install Nessus and configure settings, including scans and policies, within 3 hours. Ensure optimal performance and alignment with organizational requirements. |
| Integration with Existing Security Tools | 240 min | Integrate Nessus with existing security tools and platforms within 4 hours. Establish seamless communication and data sharing for enhanced threat detection. |
| Policy Creation and Vulnerability Scanning Setup | 180 min | Create customized vulnerability scanning policies within 3 hours. Configure scans for various assets and ensure comprehensive vulnerability assessment. |
| Reporting and Analysis Setup | 240 min | Configure reporting mechanisms and analysis tools within 4 hours. Ensure accurate reporting of scan results and actionable insights for remediation efforts. |
| Performance Optimization and Ongoing Support | Continuous | Fine-tune Nessus for optimal performance. Provide continuous support, addressing queries and concerns promptly, and ensuring the tool’s effectiveness. |